Security has become a nec essity in today’s technology world. Headlines and newsfeeds are constantly full of breaking news about security breaches and cryptors. So, how can we navigate this reality full of information and traps? How can you build your product without becoming a victim?
The Security Development Lifecycle
Not long ago, Microsoft designed what we now call the "security development lifecycle" (SDLC). The SDLC is a technique that improves the security of your code by adding the appropriate exercises and checks within each step of development. Preliminary security recommendations are very broad, covering a wide variety of possible cases. From there, each product gets its own, specially designed scope of security requirements, policies, and procedures in order to become safer against particular technology threats.
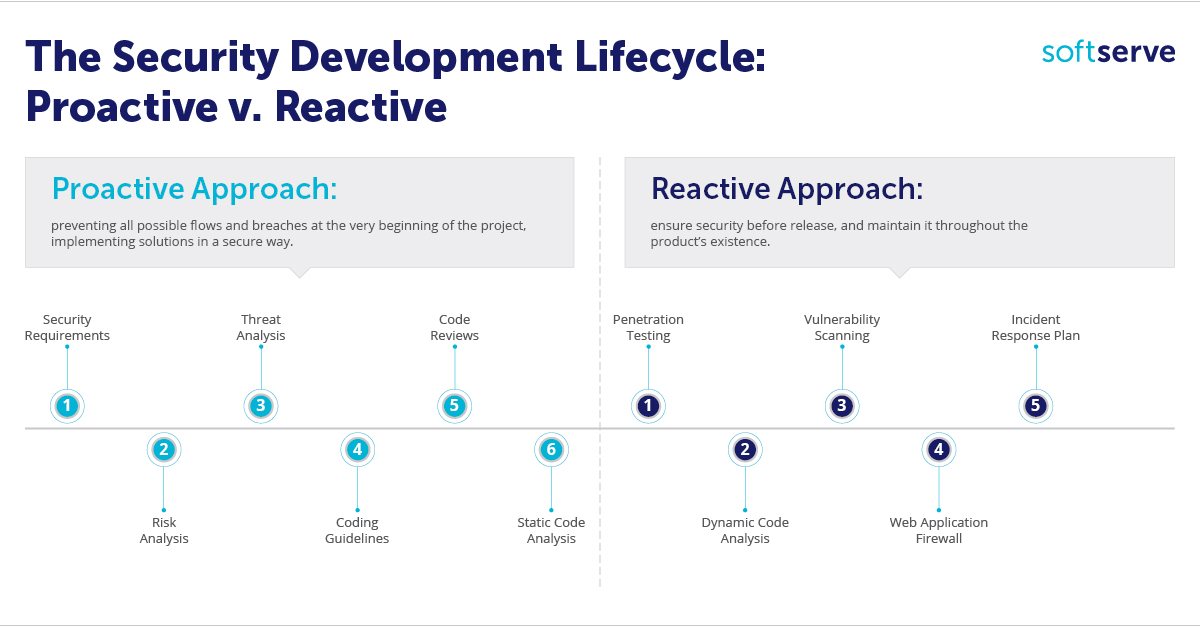
Penetration Testing
One of the most interesting techniques, for a security engine er, is to do a penetration testing of the application. Here, the work of a real hacker is imitated to uncover security flaws and issues, check the authentication and authorization management, input validation, and many other aspects of the product.
Dynamic Code Analysis
Contrary to static analysis, dynamic analysis is executed while the application is in operation, and continuously monitors functional behavior, response time, system memory, and overall performance. This approach could be easily used in continuous integration, as well as in static analysis. While automated tools cannot replace humans, it helps to accelerate and improve the work of engineers.
Web Application Firewall
A web application firewall (WAF) is a specially designed application firewall that works over HTTP protocol. It’s comparable to a very light version of IDS (intrusion detection system), but specific to HTTP. WAF contains rules against common attacks such as SQL injection or XSS (cross site scripting). Today popular solutions include using WAFs that are already within DDoS protection services, to kill two birds with one stone.
Incident Response Plan
Before the release of the product, one important thing has to be done: an incident response plan has to be created. As attack methods are continuously evolving, a security breach is always possible. The incident response plan includes all appropriate persons to contact in an emergency and the sequence of steps to perform in order to eliminate the breach. The final security review must be done before the release.
Upkeep and Maintenance
After the release and throughout each new version of the product, it’s imperative to remember security maintenance and protocols. While the most difficult security systems are the newest ones, security engineers and management should implement the response plan and maintain the product environment. This means updating all used tools, libraries, and operating systems. Employees should become used to keeping security in mind until it becomes a habit to create code in a conscious, quality, and secure manner.
Both approaches, proactive and reactive, are equally important in a creating secure environments. While it’s easiest to build your security from the ground up, often the reactive approach is needed for threats that aren’t known until the last minute. The best course of action is to strive for a balance between analytical and practical security activities, protecting your business against different security threats.
Interested in the SDLC for cloud security? Check out our latest whitepaper “Cloud Security and the Containers Approach” by Igor Beliaiev, Security Engineer.

